GnuPG Guide (GPG)
How to verify the integrity and authenticity of software?
When downloading software, it’s very important to ensure that it hasn’t been altered and that it indeed comes from the official source. This is especially true for software related to Bitcoin, such as wallet software, which allows you to secure the keys giving access to your funds. In this tutorial, we will see how to verify the integrity and authenticity of software before installing it. We will use Sparrow Wallet as an example, a favorite wallet software among bitcoiners, but the procedure will be the same for any other software.
Verifying integrity involves ensuring that the downloaded file has not been modified by comparing its digital fingerprint (i.e., its hash) with the one provided by the official developer. If the two match, it means that the file is identical to the original and has not been corrupted or modified by an attacker.
Verifying authenticity, on the other hand, ensures that the file indeed comes from the official developer and not an impostor. This is done by verifying a digital signature. This signature proves that the software was signed with the legitimate developer’s private key.
If you skip these checks, you risk installing malware that can steal private keys or corrupt files — do not install until both authenticity and integrity are verified.
To perform this verification, we will use two tools: hashing functions to verify integrity, and GnuPG, an open-source tool that implements the PGP protocol, to verify authenticity.
Prerequisites
If you are on Linux, GPG is preinstalled on most distributions. If not, you can install it with the following command:
1
sudo apt install gnupg
For macOS, if you haven’t already installed the Homebrew package manager, do so with the following commands:
1
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/HEAD/install.sh)"
1
echo 'eval "$(/opt/homebrew/bin/brew shellenv)"' >> ~/.zprofile
1
eval "$(/opt/homebrew/bin/brew shellenv)"
Then install GPG with this command:
1
brew install gnupg
For Windows, if you do not have GPG, you can install the Gpg4win software.
Downloading Documents
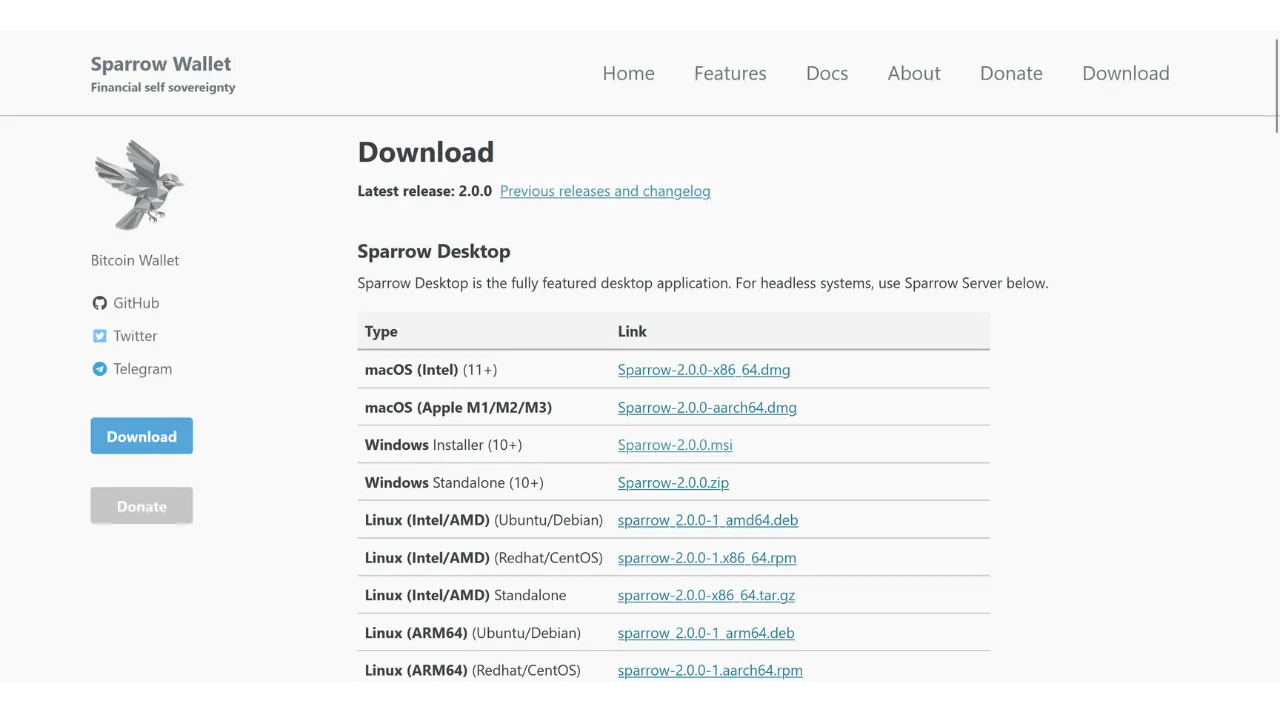
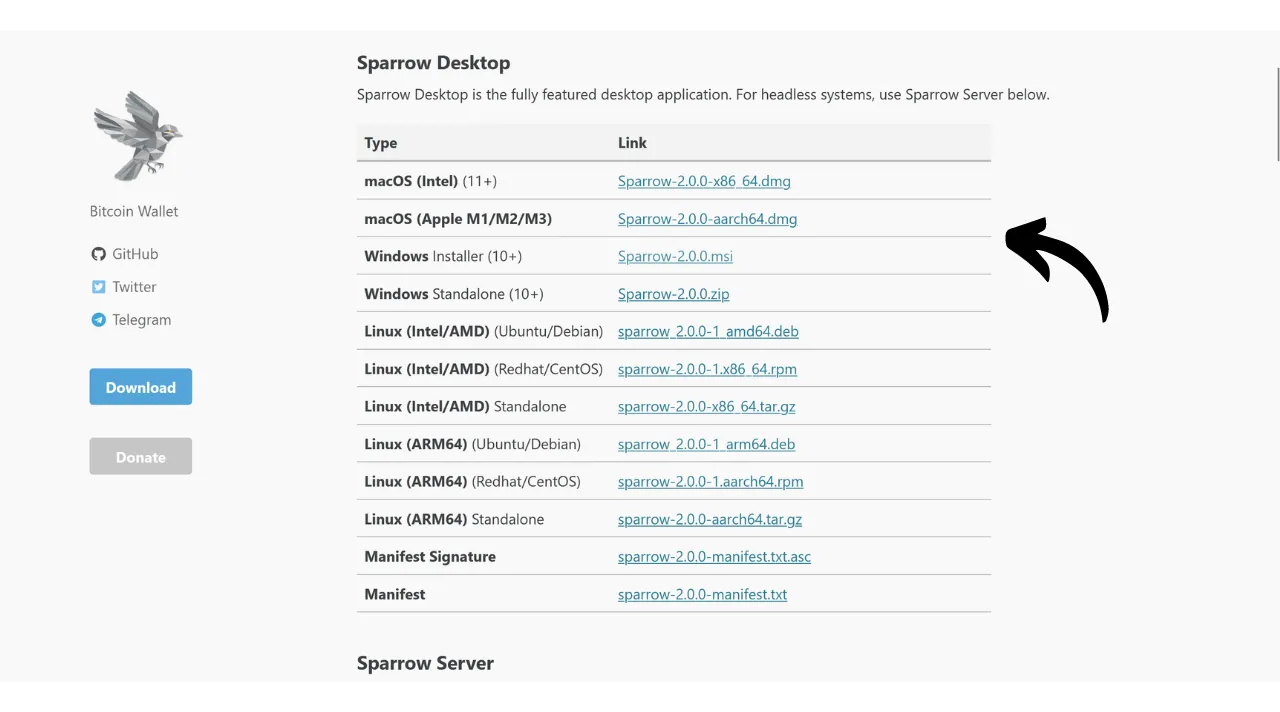
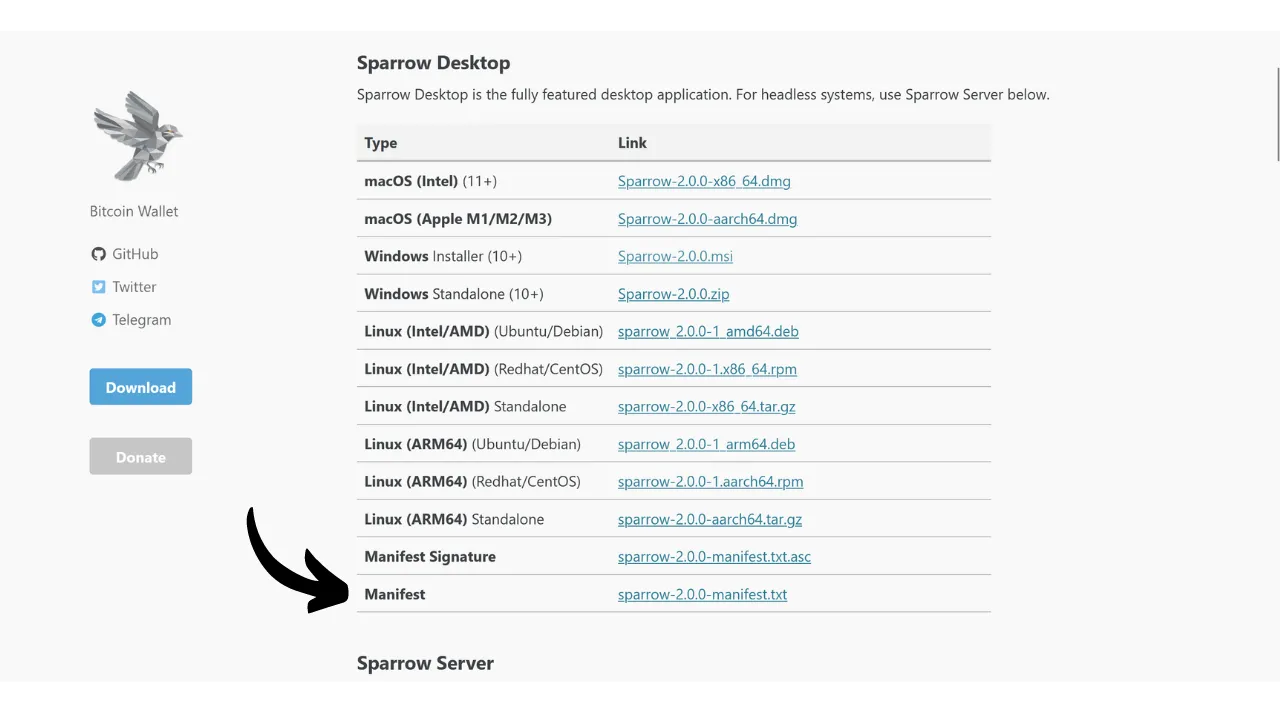
To start, we will need various documents. Visit the official site of Sparrow Wallet in the “Download” section. If you wish to verify another software, go to that software’s website.
You can also go to the GitHub repository of the project.
Download the installer for the software corresponding to your operating system.
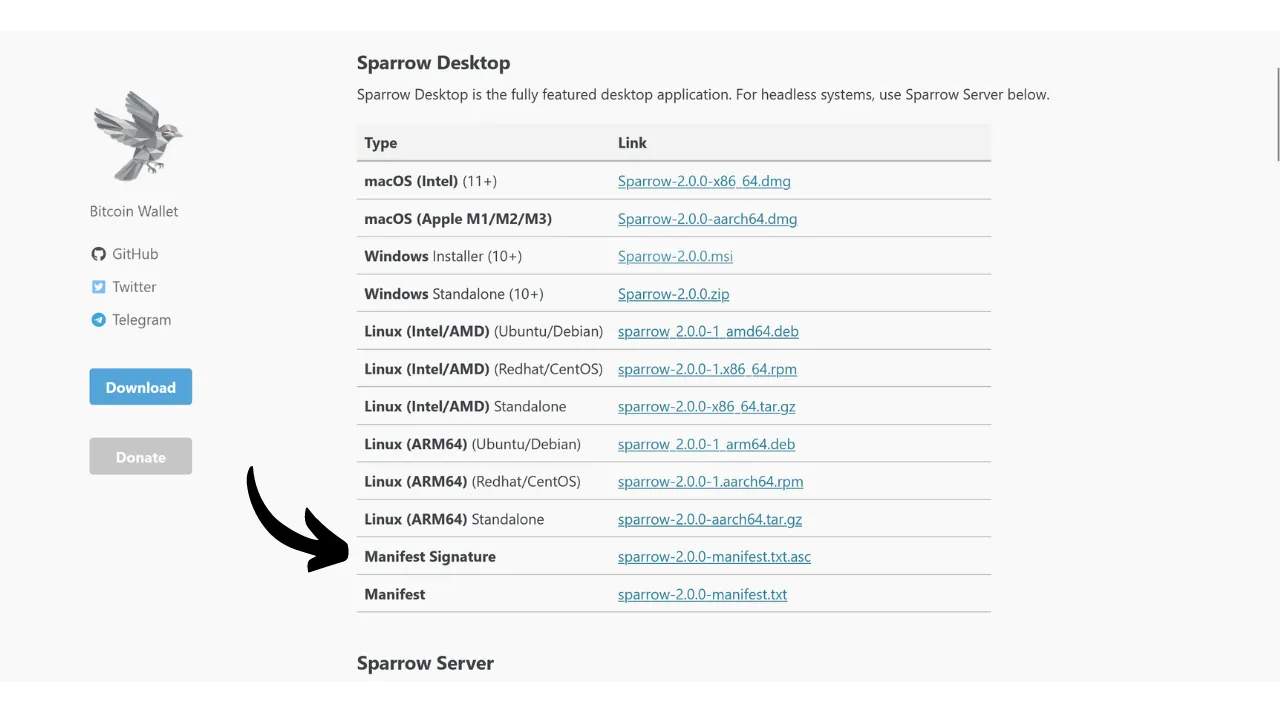
You will also need the file’s hash, often called “SHA256SUMS” or “MANIFEST”.
Download the PGP signature of the file as well. This is the document in .asc format.
Download installers, hashes, and signatures only from official release pages to reduce spoofed or tampered assets.
Place the installer, hash/manifest, and .asc signature in the same folder to simplify verification commands.
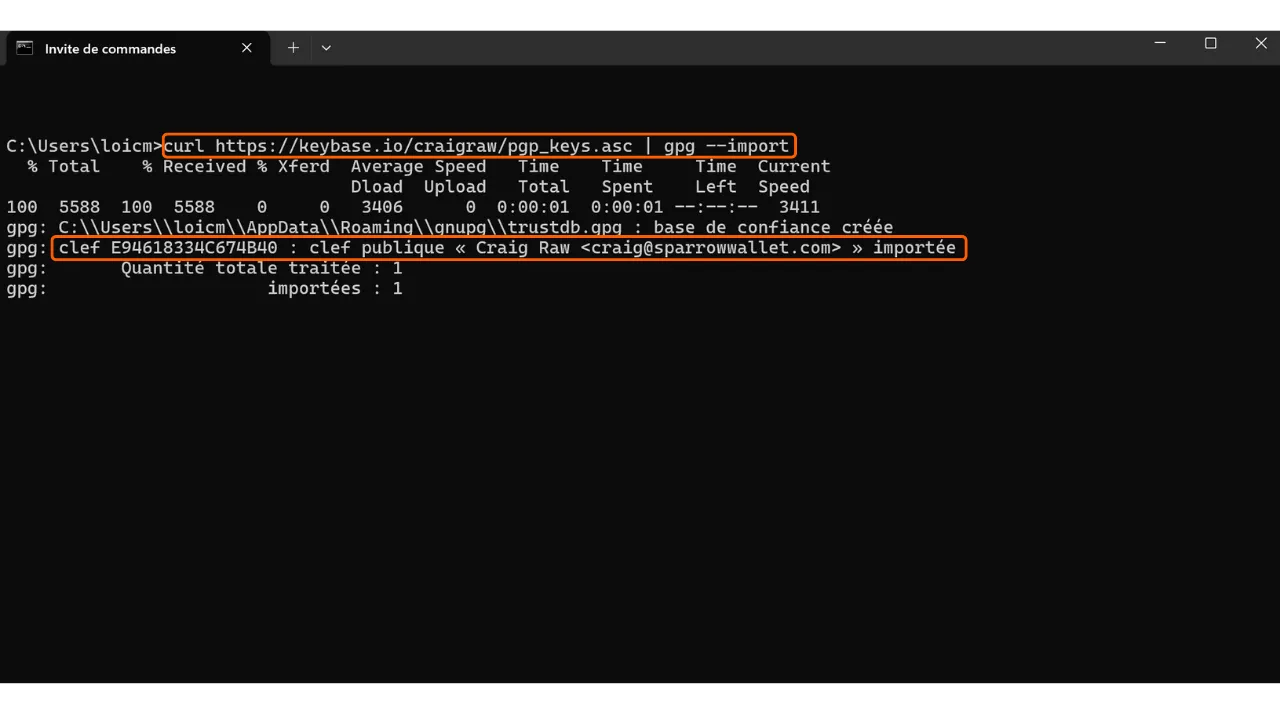
Finally, you will need the developer’s public key, which we will use to verify the PGP signature. This key is often available either on the software’s website, on the GitHub repository of the project, sometimes on the developer’s social media, or on specialized sites like Keybase. In the case of Sparrow Wallet, you can find developer Craig Raw’s public key on Keybase. To download it directly from the terminal, execute the command:
1
curl https://keybase.io/craigraw/pgp_keys.asc | gpg --import
Verify the public key fingerprint from multiple independent sources (site, GitHub, Keybase, social) before trusting it; do not rely on a single source.
Verifying the Signature
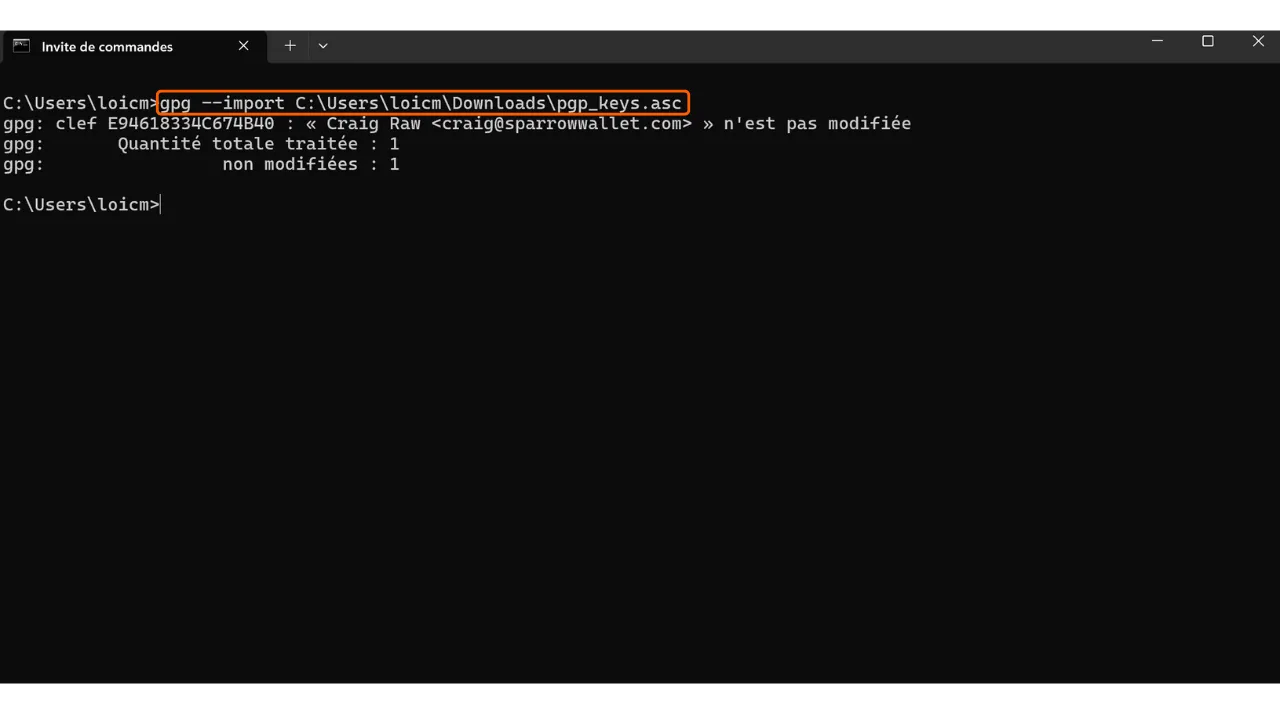
The process of verifying the signature is the same on Windows, macOS, and Linux. Normally, you have already imported the public key during the previous step, but if not, do so with the command:
1
gpg --import [key path]
Replace “[key path]” with the location of the developer’s public key file.
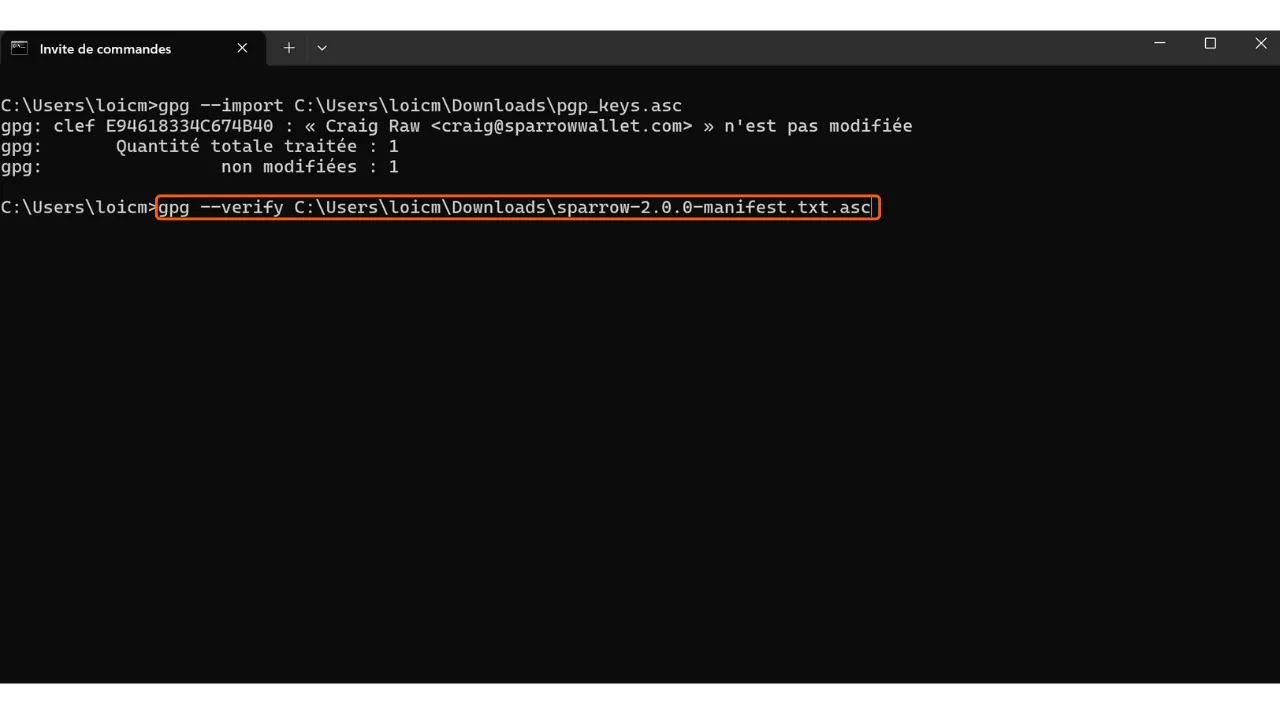
Verify the signature with the following command:
1
gpg --verify [file.asc]
Replace “[file.asc]” with the path of the signature file. In the case of Sparrow, this file is called “sparrow-2.0.0-manifest.txt.asc” for version 2.0.0.
If signature verification fails or references an unexpected key, do not proceed — the asset may be tampered or signed by an impostor.
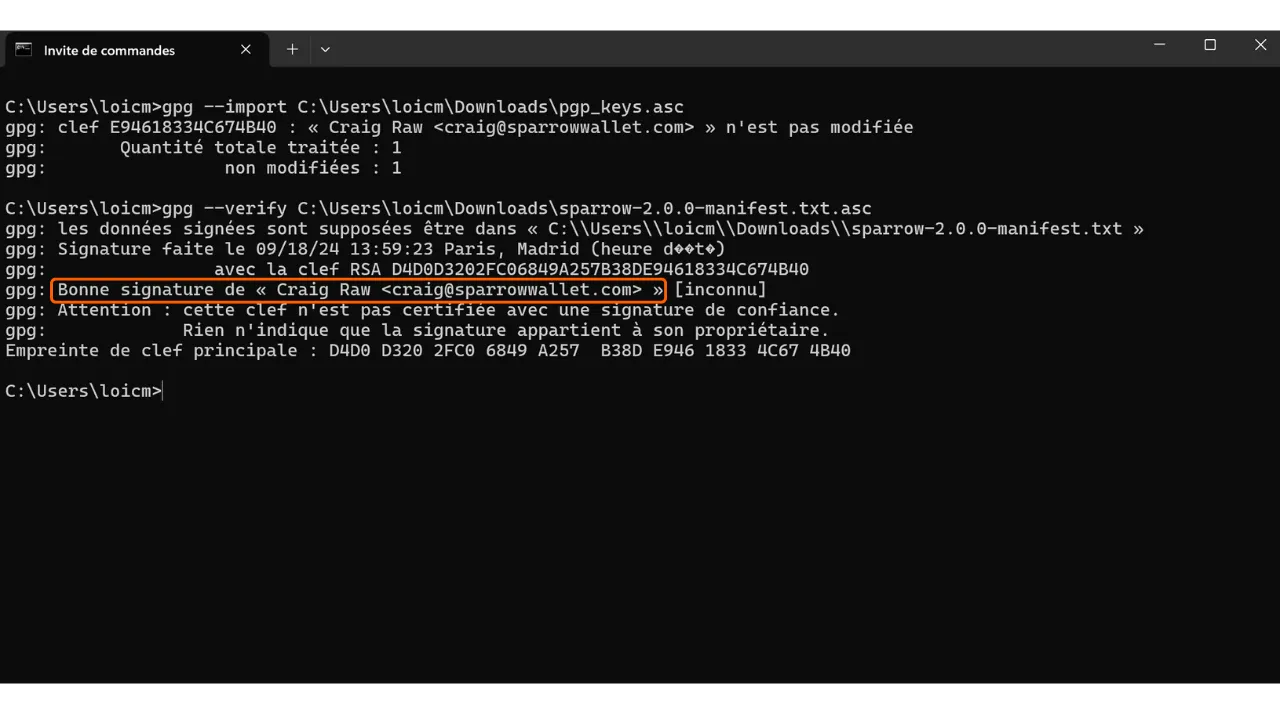
If the signature is valid, GPG will indicate this to you. You can then move on to the next step, as this confirms the file’s authenticity.
A “good signature” is only meaningful if the signing key’s fingerprint matches the developer’s independently published fingerprint.
Verifying the Hash
Now that the software’s authenticity has been confirmed, it’s also necessary to verify its integrity. We will compare the software’s hash with the hash provided by the developer. If the two match, it guarantees that the software code has not been altered.
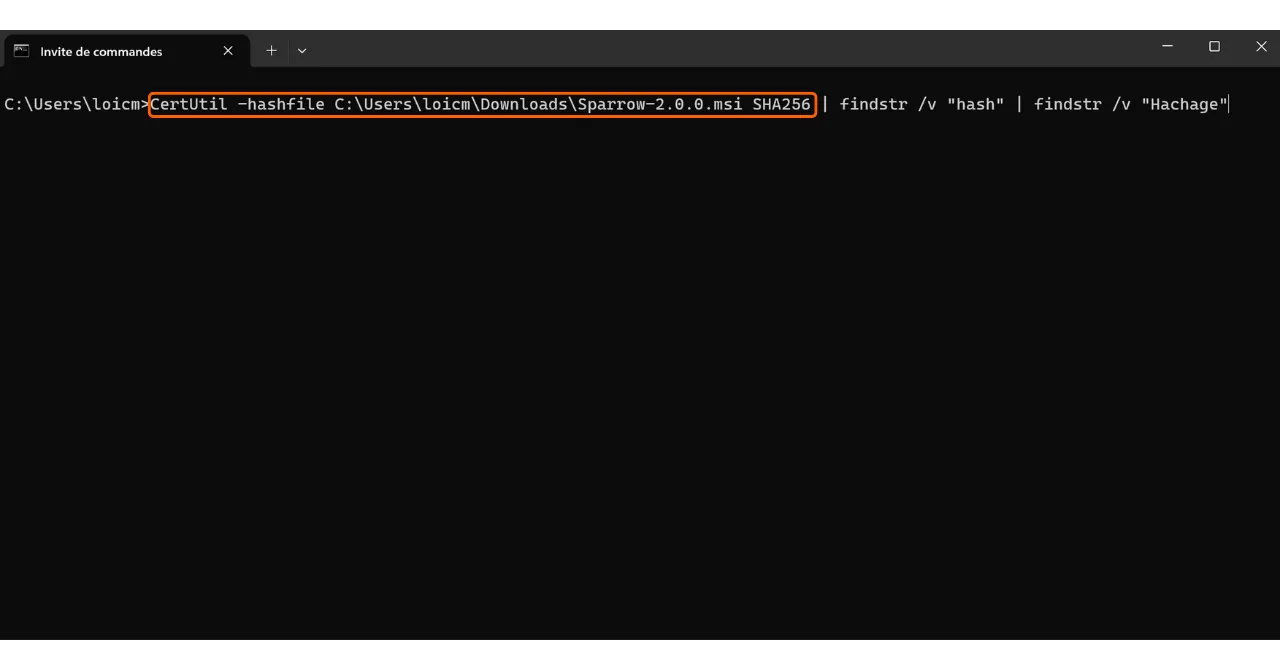
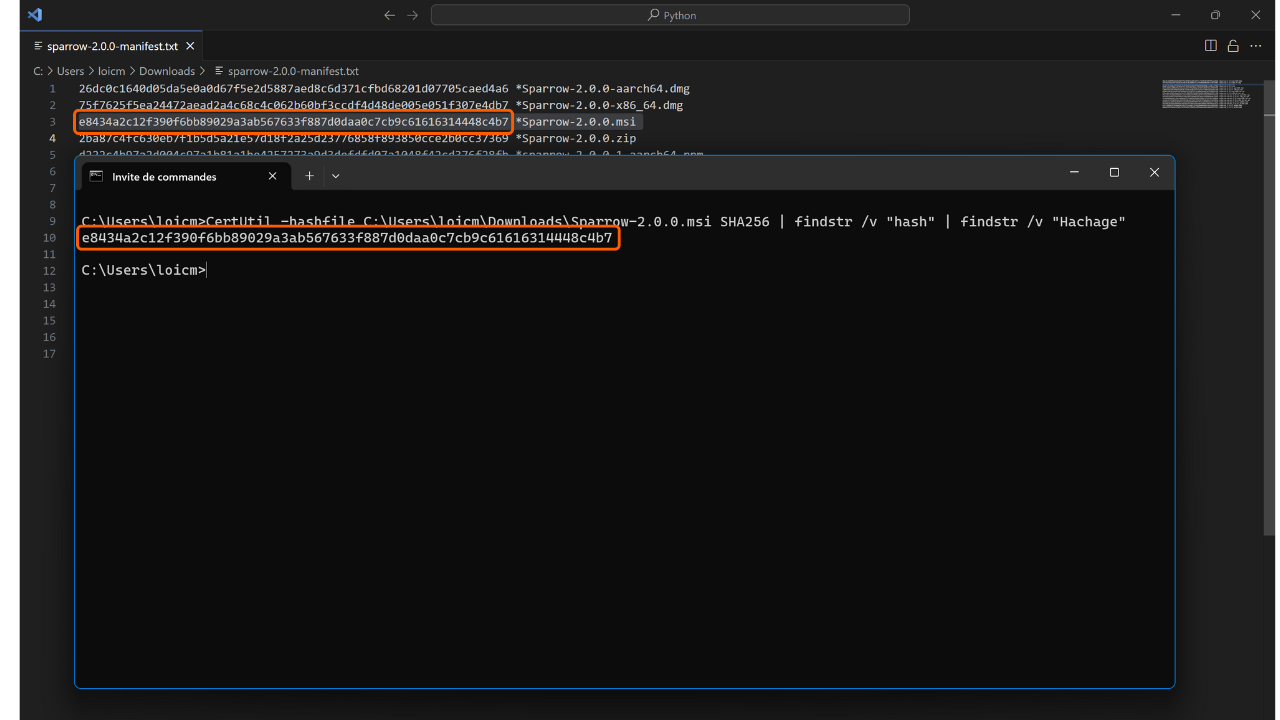
On Windows, open a terminal and execute the following command:
1
CertUtil -hashfile [file path] SHA256 | findstr /v "hash"
Replace “[file path]” with the location of the installer.
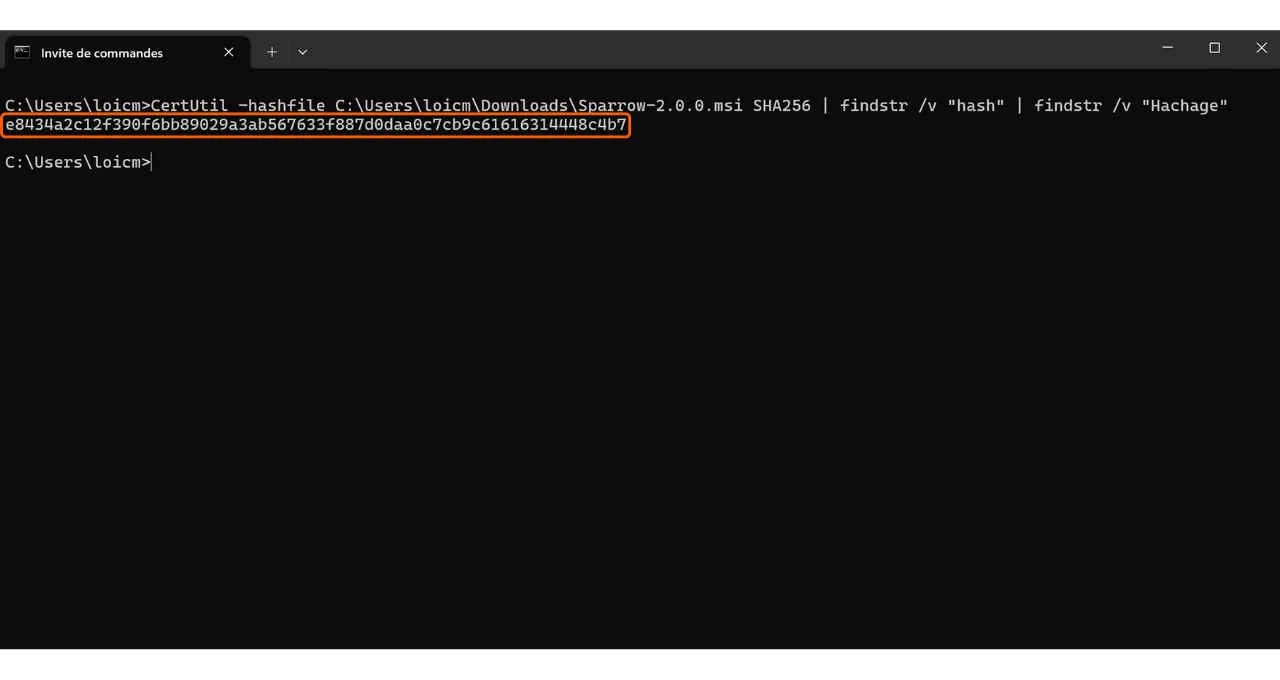
The terminal will return the hash of the downloaded software.
Some projects use different algorithms (e.g., SHA512). Use the algorithm specified by the developer for accurate comparison.
Then compare the result with the corresponding value in the file “sparrow-2.0.0-manifest.txt”.
In my case, we see that the two hashes match perfectly.
On macOS and Linux, the hash verification process is automated. It’s not necessary to manually check the match between the two hashes as on Windows.
Simply execute this command on macOS:
1
shasum --check [file name] --ignore-missing
Replace “[file name]” with the name of the installer. For example, for Sparrow Wallet:
1
shasum --check sparrow-2.0.0-manifest.txt --ignore-missing
If the hashes match, you should see the following output:
1
Sparrow-2.0.0.dmg: OK
On Linux, the command is similar:
1
sha256sum --check [file name] --ignore-missing
And if the hashes match, you should see the following output:
1
sparrow_2.0.0-1_amd64.deb: OK
If the hash does not match, do not install — re-download from the official source and repeat verification.
You are now assured that the software you’ve downloaded is both authentic and intact. You can proceed with its installation on your machine.
Repeat these checks for every update or re-install; never trust cached files without re-verification.